

by Joshua Bosell
This article originally appeared in the March/April 2022 issue of FMJ.
Healthcare is a unique industry in that operational staff and facility management staff must converge to ensure patient care is met and regulatory compliance is fulfilled. Today, the FM team is challenged in ways that have not been seen in a generation. The Covid-19 pandemic has driven the health care industry to rely upon a digital services model to ensure that physicians have safe interactions with their patients and provide a healthy environment for in-house staff and patients alike.
According to the PriceWaterhouseCoopers (PWC) 2021 survey on healthcare trends, new technologies such as mobile applications have increased venture capital by 103 percent. That same study also found that more than 60 percent of their respondents favored the use of new technologies to advance patient care. The progression and implementation of 5G allow for big data, mobile devices and the Industrial Internet of Things to assist with the decision-making and support capital and operational initiatives.
The advent of 5G will allow IoT to become mainstream, further developing the ideals of a systems-centric approach to patient service delivery. Using a systems approach to patient care would start at the dispatch with real-time location services used for mobile handsets reducing the location to near meters rather than multikilometer distances that have been used from radio tower (Lakkis & Elshakankiri, 2017). Research has evaluated the needs of emergency services using Zigbee Wi-Fi to streamline and reduce traffic-related delays — effectively shortening the maximizing the “golden hour.”
The systems approach should not only be used for patient care. Today’s FMs face challenges from environmental to inventory control to ensure that the hospital meets capital and operational expense initiatives. While HVAC/environmental control has been long a staple of operational expense control, other new technologies exist within the realm of automation including RFID networks, RTLS, and sanitization monitoring.
As with any new technology or innovation, there will be issues, including vulnerabilities. These include weaknesses in devices, risks from firmware, software (program) and even the resilience of the hardware. However, at its core is the lack of general understanding and consensus of how to manage such a network of converged technologies. Facilities must be able to means-test the technology and partner with an equally established vendor to manage the operational life cycle.
With the pandemic driving hospital systems to reduce their floor space to balance the virtual delivery model, FM staff will be challenged in new ways, including cybersecurity. Forescout’s 2020 survey on cybersecurity evaluated several sectors of the economy from finance, health care to public/government. What was found was that at the highest risk for cyber intrusion was access control and HVAC automated systems — both ranking No. 2 in all sectors, only being surpassed by HL7 gateways and pneumatic tube systems health care. The question becomes who is responsible for safeguarding these integrated systems, and what should facilities do?
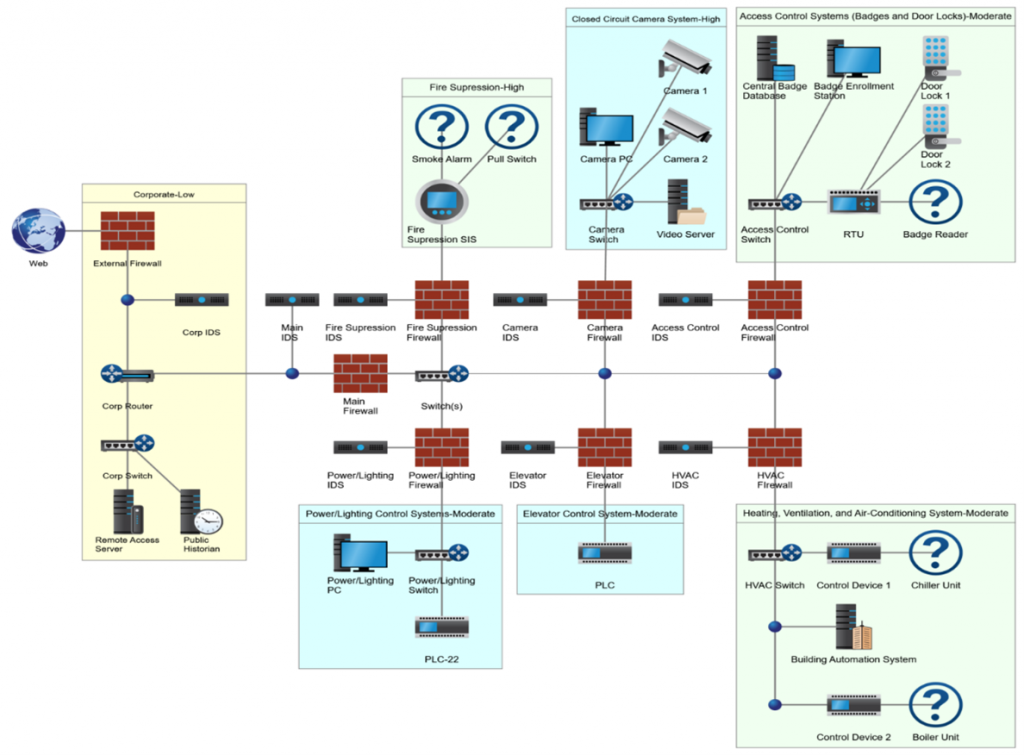
Figure 1 depicts an integrated technology approach that provides a sustainable, secure converged network that allows both IT departments to become fully vested partners of facilities outside of their current role of protecting IT assets.
The convergence of the corporate (IT) and operational (OT) networks requires changes and updates to the hospital’s delivery systems and the vendors that support them. The trades play a specific and integral role in supporting the implementation of the network. The building automation industry has a unique position as this trades area has specialized in operational technologies. Unfortunately, due to the fast-tracked use of IoT, OEM manufacturers have developed the methodologies to deploy their systems and have filled the technology gap that their representatives have left. Therefore, the building automation industry, like their healthcare customers, must make changes to support such opportunities.
Issue one: An industry in transition
To be competitive, midsized to large organizations with building automation divisions could update their go-to-market strategy to include integrated infrastructure. However, to be successful, these organizations must modify their strategic approach to today’s industry to adopt a new mentality as a “Master Integrator.” There are three key areas where the industry must change – networking, secure design, and training.
Building automation organizations has been solely reliant upon a service model that supports the core competencies of the trade, avoiding regulatory requirements. However, as technology advances, IT/OT convergence will include big data and artificial intelligence. Service providers must treat this opportunity as a competitive advantage and distinguish themselves as a technology organization, not a division of a mechanical contractor. This advantage, however, is incumbent upon making organizational structure changes, including training and education.
The next generation building automation organization would deploy a team managed within the regional or national accounts division to unify inter-divisions currently siloed. The team would include specialists in the “core competencies” of building automation, video surveillance, access control, and fire/life safety. In addition, to assist with today’s challenges of the Internet of Things, a Network Engineer would be added to help with the deployment and assist with the network strategies, coordination, and management of the software development lifecycle, including the deployment and commissioning. This team, being diverse, can either be virtual or collocated.
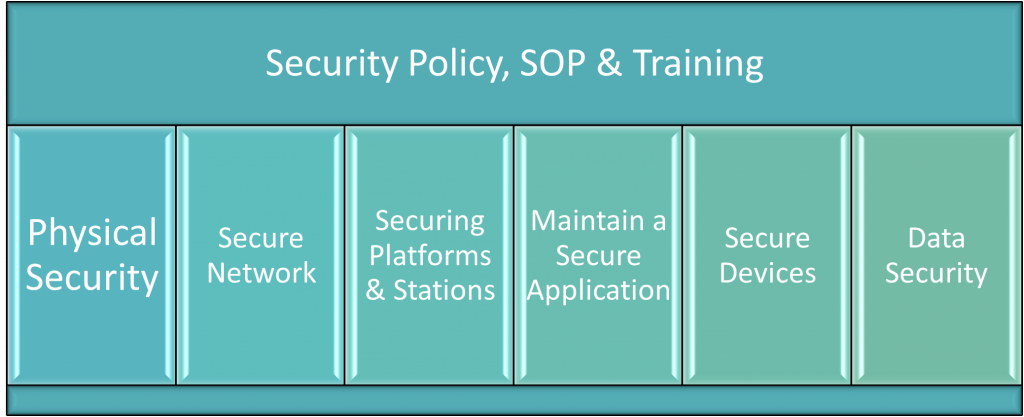
Finally, along with creating a network integration team, the organization must identify its security policies. The goal of establishing a standard is to make governance around secure engineering, programming, and commissioning that insist upon application-based security features. The security policies should be unique to the building automation division and separate from the information technology departments’ corporate security policies required for corporate networks. This is partly because programmable IoT devices are susceptible to zero-day vulnerabilities and other IP-based vulnerabilities, including those that affect the confidentiality, integrity, and availability of the device, and ultimately the network itself. Also, a fundamental way of hardening software is through repeatability. Finally, standardization in many cases, including having a policy that dictates how programs are developed mitigates risk, and threat exposure when deployed.
Issue two: Necessary organizational changes required
The investment and use of the internet of things within the healthcare industry is a choice to provide the best patient care. Integrated systems achieve organizational success through increasing profits from patient referrals and cost savings initiatives from operational management. While the long-standing focus of controlling operational expenses has been through energy management of the mechanical systems, hospital systems can now provide comprehensive services through connected medical devices. Thus, further lowering operating fees, real estate costs and increasing the Return on Investment. Like their building automation partners, the hospital system’s facility management must make structural and process changes to their delivery methods.
Investment in training and coordination between divisions makes the service model move toward the Information Technology division. The convergence of operational technology with information technology also has lent itself to the confluence of personnel. Operational staff must be ready to be technologically savvy and maintain an active awareness of the systems they serve or control, including big data devices like that of Real-Time Location Services devices to connected medical devices. Even with troubleshooting, skilled labor must be capable of troubleshooting electronics as well as mechanical systems.
While the Internet of Things has similarities to IT, the Operational technologies remain a gaggle of legacy technologies such as Modbus RTU, LON, and BACnet MS/TP. These protocols allow for “open” integration but are limited to their own specific set of constraints during deployment. Thus, while the transition to a fully deployed IP-based IoT and wireless 5G is integrated, the existing infrastructure must depend upon long-standing techniques to prevent 21st-century risks that include cybercriminals. Therefore, robust investment in IoT is a must. In addition, the procurement of, and sustainable management practice of protecting such an integrated system through IoT security processes, is rooted in good security practices. This will require the hospital system to establish a project selection methodology that takes these risks as part of the vendor selection process.
The effect of the Internet of Things will continue to trend toward full convergence between operational technologies and information technologies. As a result, the end-user and the technology providers must be prepared to move technology from proprietary networks such as TIA-485 (BACnet) and (H)ealth (L)evel 7 to IP-based devices supported singularly by 5G. This means that as new technology develops and certainly matures, healthcare systems must identify whether they are cost-beneficial and assist with the mitigation of risks as part of their operational model. As part of the analysis, new jobs, new processes, and federal regulatory final rules on patient information protections must also be considered.
To further challenge the service partnership, the service organization must develop a diverse technology team in handling the secure design, integration, deployment, and support of provisioning big data and the complex nature of the infrastructure – moving from a construction model to a hybrid model that includes activities of foundationally IT-centric tasks including DevOps, network engineering, and cybersecurity. In the end, it will be incumbent of the service provider to change their service model to ensure they can be a supporting voice when health systems choose to deploy IoT. As a result, the service provider will strengthen their partnership while shifting the manufacturer’s strategic initiatives from an executing role to supporting one, thus increasing direct revenue streams for the service provider.
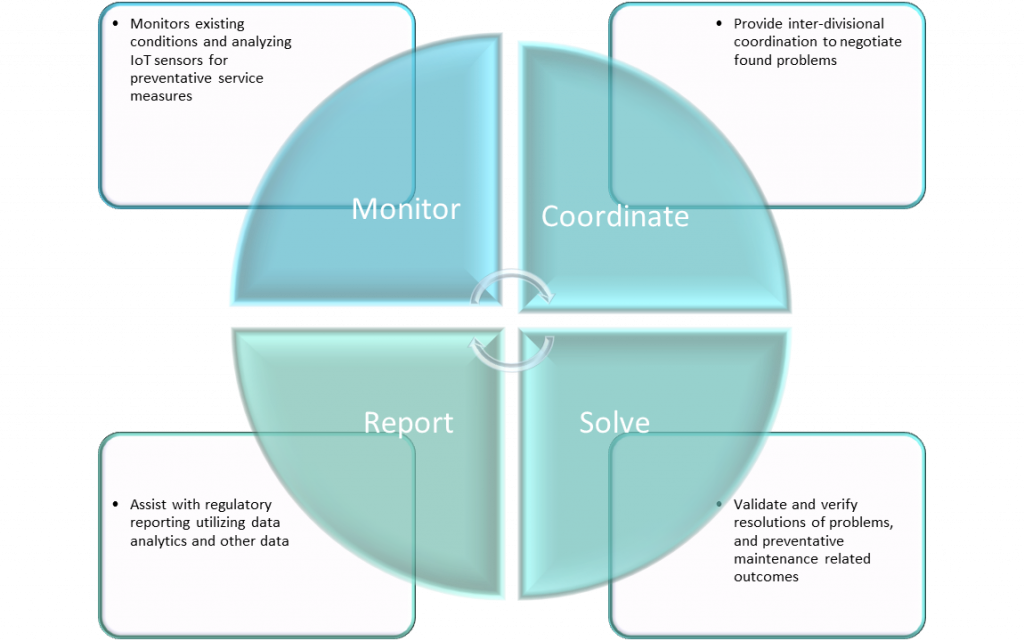
With both the healthcare industry and the supporting supply industries, the Internet of Things is a game-changer. By providing an outcome-based approach, IoT has allowed the streamlining of the service model to use big data to evaluate and validate project financials; the industry has become more efficient. Unlike rudimentary technologies of the ’80s and early ’90s, the use of IoT has presented opportunities to small and medium-sized organizations and organizations like nationally recognized healthcare systems to maximize operational and capital expenditures. However, it will be up to the facility staff of each healthcare system to establish both the mode and means of integration, deployment and sustainability.
About the author: Joshua Bosell, MSIT, PMP, is the strategic project manager for EMCOR Services in Indianapolis, Indiana. With more than 15 years of experience in IoT and the health care sector, he specializes in converged networks, IoT integrations and migrations.
FMJ, the official magazine of the International Facility Management Association (IFMA), is written by and for workplace professionals and is published six times a year. FMJ is the only magazine that draws on the collective knowledge of IFMA’s global network of thought leaders to provide insights on current and upcoming FM trends.
